I received an email from someone referring to him/herself as “nz”. NZ solved the challenge by creating a pseudo block header with the correct timestamp (and very low difficulty) using a python tool whose github address is included in NZ’s e-mail.
Hi, I cleared the challenge.
I got access by emulating the following block in the chain with the desired date and lowering the difficulty to the minimum. Modifing a python script
https://gist.github.com/ChristopherJohnston/42b4a8af11c2d02ef2cc2c972fe6ee5d#file-block-py
Since it doesn’t needed internet access i just inputted the results.
Password=A459D5B9-C619-432B-9176-2558E39028C8
BlockNumber=675649
BlockVersion=536870912
PrevBlockHash=000073131f4a52322751499ed6f6f587927d0a14d6c5f4a29d565bda812caa21
MerkleRoot=e5bbdef9f34dc9337c69c5adcd74d9eb606c4e09b4d1ff7d4557ebab6c1be591
Bits=520159230
Nonce=67778
TimeStamp=1622067305
I verified that these parameters do work:
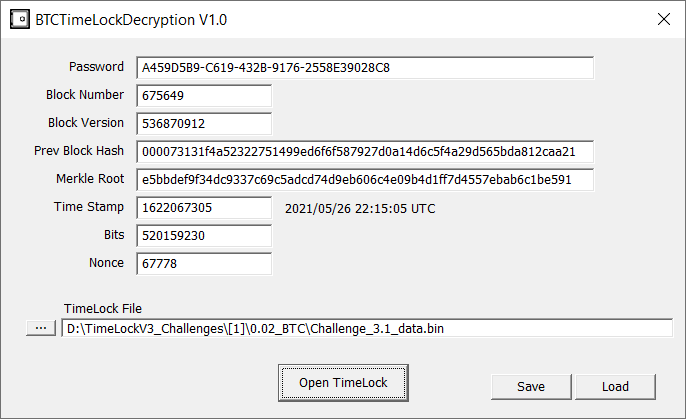
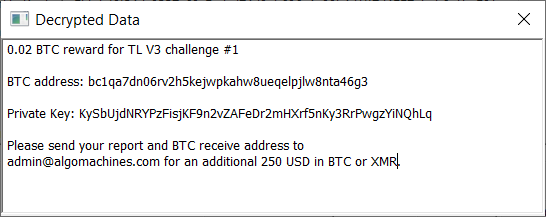
I regard this as more of a bug find than a hacking solution. My intention was that no solution would be possible unless the computed block has the correct timestamp AND a difficulty on the same order as we expect the BTC blockchain to have. Clearly this failed on the second point. So I will debug this problem and then re-issue this challenge.